At Sunset Technologies, we understand that the security and uptime of your digital environment are crucial. Our dedicated approach to cybersecurity not only protects against a wide range of cyber threats but also ensures maximum system uptime. This means your business operations can run smoothly without interruption, leading to increased productivity and reduced downtime. Our cutting-edge technology and expert knowledge offer robust safeguards for your digital assets, providing you with peace of mind and the uptime you need to thrive.

We Shield Your Business From Cyberthreats
SECURE YOUR DIGITAL HORIZON WITH SUNSET
OUR SEVEN-STEP APPROACH TO KEEPING YOUR DATA SAFE
Much like biological viruses, there are many ransomware threats circulating the web. Some are well known, some are new, and others not yet known or developed. With every occurrence, the sophistication of these viruses increases in a multitude of ways, including how they spread and how they encrypt data. Below you can read how our seven-step approach, based on the five missed standards, helps protect our clients.
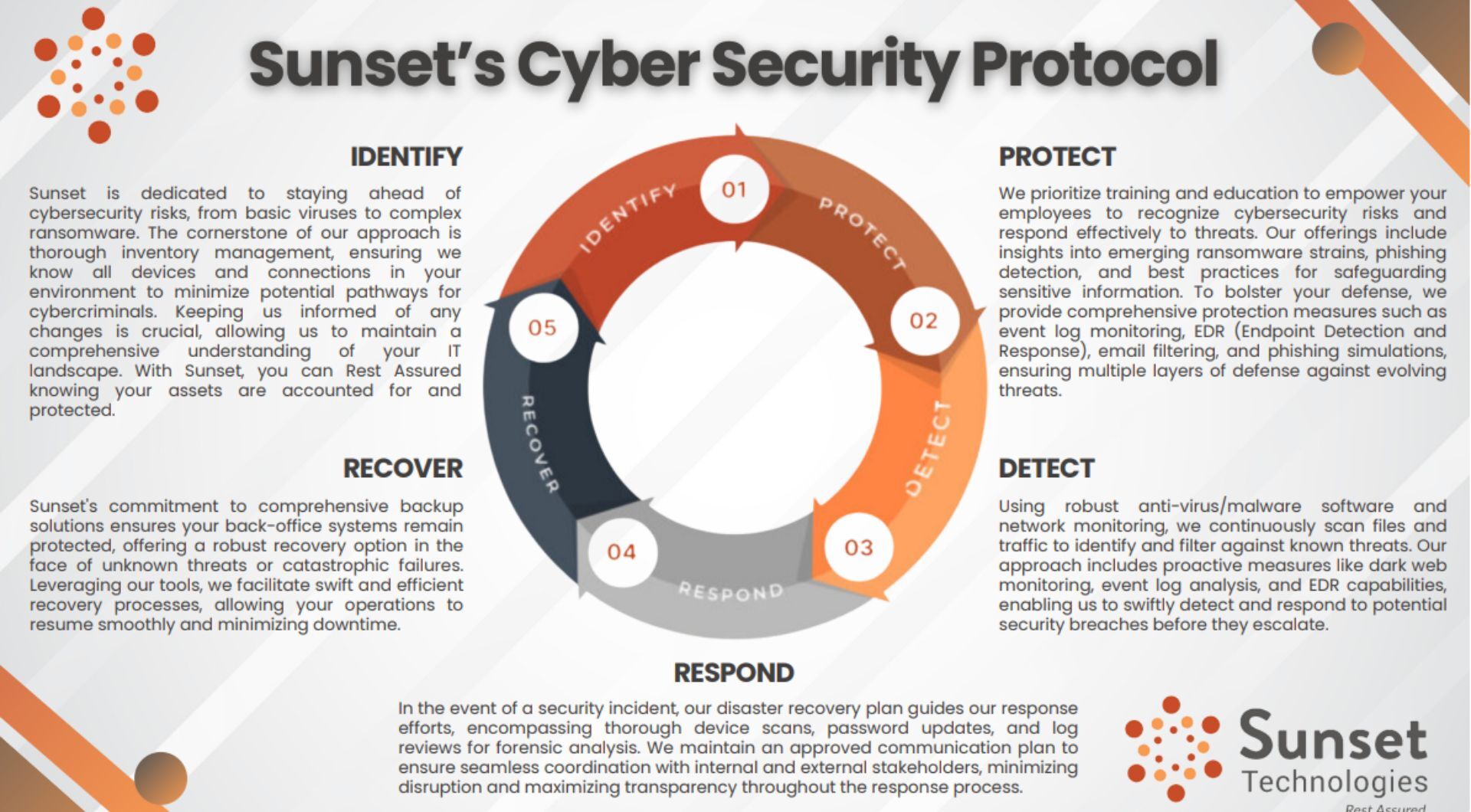
 Identify
Identify Protect
Protect Detect
Detect Respond
Respond Recover
Recover
1. INVENTORY (Identify)

The best place to begin any security effort is to know all the pathways of entrance for a cyber-criminal. In short, you must know all the devices and connections that are in your environment. It is also critical to keep your IT partner up-to-date on any changes. Many times, customers will simply plug a “new thing” into the environment without telling their IT partner. This introduces risk as a possible new doorway for cyber-attacks.
2. EDUCATION AND AWARENESS (Protect)

The most important step in our process is to create awareness about these threats. We offer training and education to help your employees understand about cybersecurity risks, new ransomware strains and best practices for spotting phishing attempts, suspicious emails, and other security risks. Empowering and encouraging them to be proactive increases awareness and decreases overall risk.
3. ANTI-VIRUS/MALWARE & NETWORK MONITORING (Protect & Detect)

People are being targeted through more sources than ever – email, ad networks, mobile applications, and devices. Anti-virus/malware and network monitoring examines all files and traffic, then filters them against all known threats. We keep virus definition files updated to protect these systems.
4. PATCHING (Protect & Detect)

The most basic layer of protection is to monitor and patch all computers and applications. Utilizing the latest patches, we can address all known operating system vulnerabilities. The patching process provides this basic layer to operating systems, especially once a security flaw is uncovered. We provide the latest patches to ensure your systems are running at peak performance and that all system vulnerabilities are addressed.
5. FIREWALL WITH INTRUSION PREVENTION SYSTEM (IPS)(Protect, Detect & Respond)

Every firewall provides a layer of protection; however, our IPS supplements the predefined rules of the firewall filter. It inspects communications and analyzes traffic patterns in real time to detect malicious activity and prevent attacks. This dual function has a significant impact on business security, reduces cost as it simplifies device management, which in turn increases business profitability.
6. DISASTER RESPONSE PLAN (Respond)

As business owners, we don’t have insurance because we plan to use it; we have it in case of an emergency, so we are prepared. The same can be said for creating a disaster response plan. It is essential in mitigating the fallout from a breach. A proper response plan starts with a complete inventory as discussed earlier. It will also include making sure all devices are scanned and passwords changed, logs reviewed and saved for forensic analysis, and confirmation that all systems are operating as expected. A complete response plan should also include an approved communication plan that covers both internal and external entities.
7. BACKUP AND DISASTER RECOVERY (Recover)

There is sometimes a gap between when a threat is first introduced and when we receive notification and can develop a remedy. We do a full- system backup to protect your back-office systems. This enables us to stay on top of things when an attack occurs and provide a recovery option for unknown threats in even the most catastrophic failures.